|
Hi,
A little while ago you signed up for updates about HTTP Toolkit.
I generally limit this to (very) intermittent product release announcements, but once again this year multiple people have reached out to ask about Black Friday deals, so it seems like a great chance to combine a discount offer with an update talking through all the latest changes in HTTP Toolkit.
Black Friday Deal
First up: this weekend is Black Friday/Cyber Monday, and so until Tuesday (November 28th) there's now a 50% discount on new annual subscriptions. Just enter BLACKFRIDAY as the coupon code during checkout.
That's on top of the normal discount for annual subscriptions (approximately 30%, compare to paying monthly) and that's a recurring discount - if you sign up at that price now, your subscription will stay discounted for as long as your subscription runs. Enjoy :-)
If you were thinking about signing up for Pro eventually, or you’re just looking for an easy way to help contribute to HTTP Toolkit’s development and support open source, this is the perfect time.
🚀 Sound good? Sign up for HTTP Toolkit Pro now 🚀
Product Updates
With that out the way, let's do a very quick run through what's been happening in HTTP Toolkit recently:
HTTP Send
HTTP Toolkit has a new 'Send' page coming soon, providing a fully featured HTTP client. With this new functionality, you'll be able to compose and send HTTP requests to test your target APIs, and resend intercepted requests from elsewhere (with your own modifications too, if you like).
This is close now, and looking for alpha testers! If you're interested in giving this a go, just reply to this email and I'll set you up.
Android 14
Android 14 support went live recently, just before the official Android 14 release itself, and getting this working has been quite the journey (more info on the blog).
This is now fully supported in HTTP Toolkit, with fully automated system certificate injection. There were some significant changes here, and as far as I'm aware it's not fully supported anywhere else. This may also affect Android 13 users using certain rooted device setups (you can check any device by testing whether the new /apex/com.android.conscrypt/cacerts folder is present).
Everything required here should auto-update, so you won't have any problems there from now on, but do get in touch if you see any issues you think might be related, and I'd highly recommend reading through those recent blog posts if you'd like to learn more about Android's certificate internals.
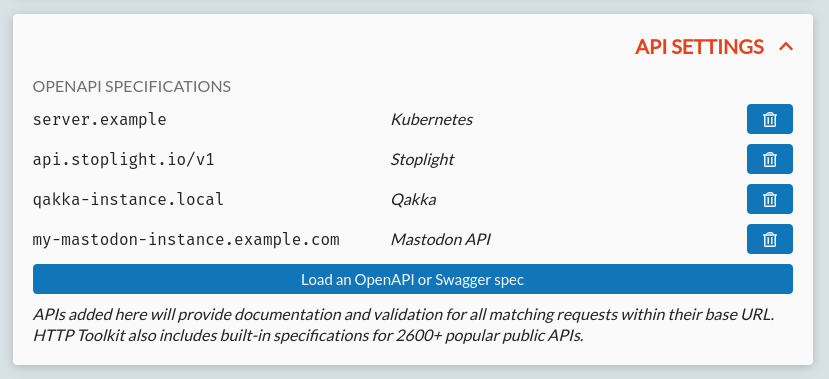
OpenAPI-Powered Interception
Earlier this year, the built-in API integrations were expanded to cover hundreds more APIs (more detail on Twitter/X).
In addition though, the internals powering this are now exposed, so Pro users can add their own APIs too, using OpenAPI or Swagger specs. That means you can now add custom validation & debugging metadata to requests to any known APIs, including your own self-hosted or internal services, directly within HTTP Toolkit.
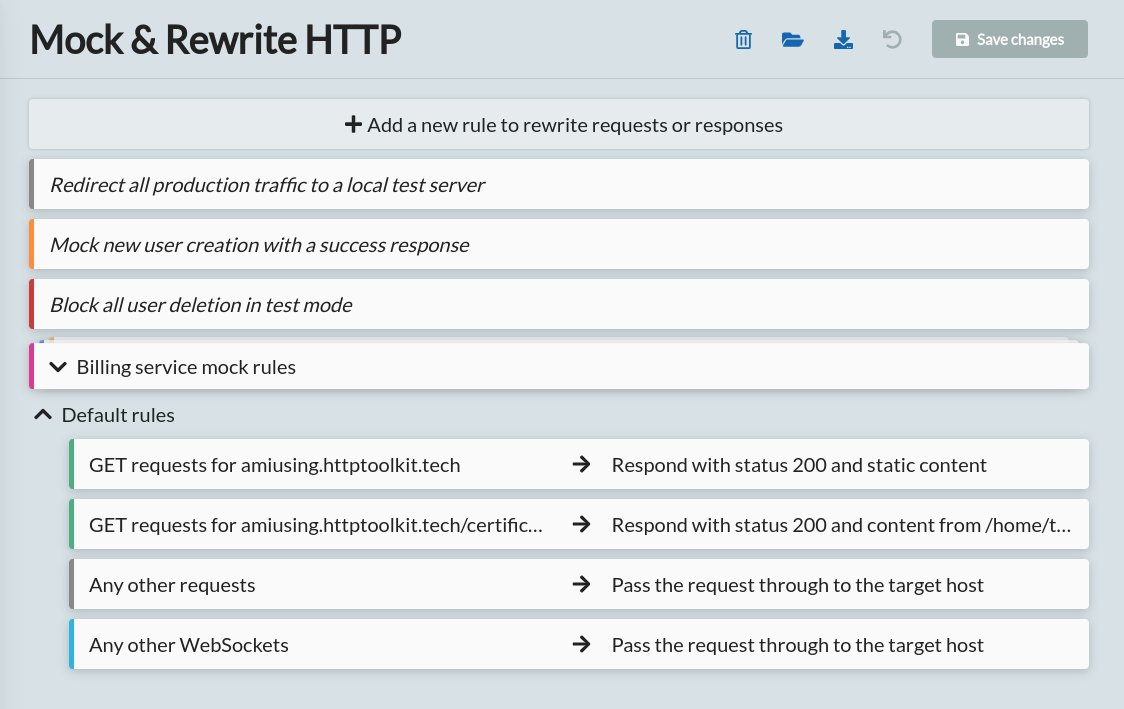
Rule Debugging Improvements
It's now much easier to debug and manage your rules, in a few ways:
- You can provide every rule with its own custom alias, so you can remember why it exists.
- Every request that wasn't passed through unmodified is now highlighted with the Mock icon in the View page list, so you can see at a glance which requests were modified.
- Each request that wasn't passed through shows a little icon in the top left, saying which rule it matched, and linking directly to the rule so you can debug and tweak that further as required.
Mobile Interception Progress
As many of you may be aware, HTTP Toolkit has been funded as part of the EU's Horizon fund (via NLnet) to work on some revolutionary new techniques for automatic targeted mobile app interception.
In the medium-term, this is going to mean automated iOS support in HTTP Toolkit, and significant improvements to Android interception (precise targetting, no VPN required, and automatic certificate unpinning), making this both simpler to use and more powerful than any other tool that exists.
Right now, that's still in progress, but if you're interested in this you'll definitely want to take a look at https://github.com/httptoolkit/frida-interception-and-unpinning.
That repo contains the latest scripts that will power this, which for Android are now in a state where they're ready for real experimental usage. You can use this with Frida to do fully automated interception of any target Android app, without any other setup on the device. No proxy configuration, no certificate fiddling, no VPN, no unpinning setup - just run Frida on the device, run the scripts, and see everything immediately.
If you have a minute, give it a quick test and share feedback in that repo. Watch this space, as that will soon be fully integrated into HTTP Toolkit (via the new Frida-JS library that's also part of this project) to allow you to do this with one click directly from HTTP Toolkit itself.
International Billing Improvements
If you're interested in purchasing HTTP Toolkit Pro, but you're based somewhere where credit cards often aren't the preferred online payment method, until earlier this year it was a bit tricky. That's now resolved though with a new payment provider (PayPro Global) who provide much better handling for the world beyond North America & Europe (and also provide a backup payment provider generally, making HTTP Toolkit a little more resilient to any issues with Paddle).
Customers in a wide range of countries will now see PayPro running the checkout instead of Paddle, and can pay with new methods like Pix, iDEAL, WeChat and similar. If you have any feedback on this, or you're in a country where you think PayPro would be better but it's not enabled by default, do get in touch.
Much much more...
I won't cover every tiny change in too much more depth, but there's also been lots of hard work in the details elsewhere:
- Support for automatic interception of Bun, Deno, Snap-installed browsers, Electron apps on Mac, and Python's AioHttp.
- New 'contains(x)' and 'headers' filters to search the contents of everything, and the contents of all headers in one go.
- HAR export improvements, including websocket message export.
- Context menu support - you can now access features like pinning, request export, and turning requests into rules directly from the context menu on each request row.
- A new 'Forward to Host' rule to redirect WebSocket traffic.
- A new narrow UI, allowing you to use HTTP Toolkit on smaller screens, or in a split-screen setup with a browser.
- Detailed info on messages that can't be decoded (e.g. corrupted gzip data), showing the failing raw data and detailed error messages.
- All sorts of new posts on the blog covering recent changes and exciting news in the world of HTTP.
- Lots of much smaller UX tweaks, bug fixes & little updates throughout.
Share your reviews of HTTP Toolkit
I know for many of you, the free core functionality works perfectly and so you don't feel the need to pay towards development at all. That's great! It's excellent to see HTTP Toolkit being useful to so many, and HTTP Toolkit is going to stay with its current 99% gratis model for the foreseeable future.
If you're in that position though, but you'd still like to do a small thing to help support HTTP Toolkit anyway, please share a review. Reviews on all public sites and listings make a huge difference to getting the word out, expanding the community, and helping other users to find HTTP Toolkit and understand its pros & cons.
If you have just 1 minute, it would be great if you could click the heart icon and leave a quick review with your thoughts at https://alternativeto.net/software/http-toolkit/about/.
Of course, if you have more time, reviews on Sourceforge, g2.com, and in the Google Play store are more than welcome too.
That's everything for now. As ever - thanks for all your support and messages, feel free to share feedback and vote for ideas in the GitHub repo, enjoy the Black Friday deal above, and do get in touch if you have any other questions or comments at all.
Thanks,
Tim
|