|
Hi,
A little while ago you signed up for email updates about HTTP Toolkit.
This mailing list has been quiet for a little while (I had a baby!) but it's back to business now - I have been very busy recently (alongside many wonderful open-source contributors) and there's plenty to cover. Let's dive in:
Black Friday Deal
First up: this weekend is Black Friday/Cyber Monday, and so until Tuesday (December 2nd) there's now a 50% discount on all annual Pro subscriptions. Just enter BLACKFRIDAY25 as the coupon code during checkout.
That's on top of the normal discount for annual subscriptions (approximately 30%, compared to paying monthly) and that's a recurring discount - sign up at that price now, and your subscription stays discounted for as long as it runs. Enjoy :-)
If you were thinking about signing up for Pro eventually, or you’re just looking for an easy way to help contribute to HTTP Toolkit’s development and support open source, this is the perfect time.
🚀 Sound good? Sign up for HTTP Toolkit Pro now 🚀
(But also: keep reading for product updates, or scroll to the end to vote for what comes next)
Product Updates
With that out of the way, let's run through some of the big new highlights in HTTP Toolkit recently:
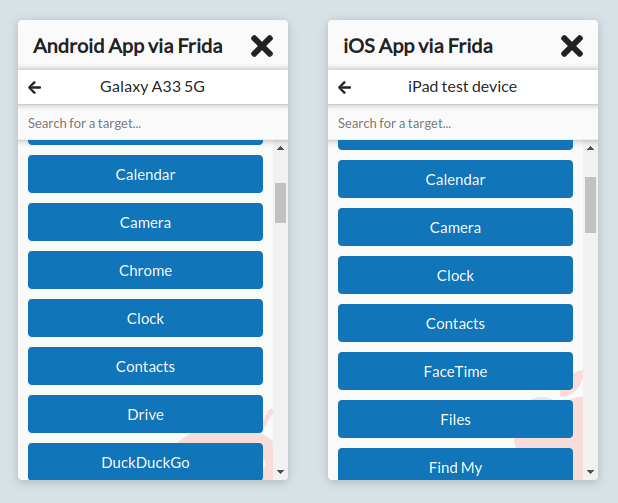
Automatic Interception with Frida on Android & iOS
On rooted Android & jailbroken iOS devices, HTTP Toolkit can now:
- Automatically set up & launch Frida
- List the targetable apps directly on your computer
- In one click, capture all traffic from any specific app, without interfering with any of the rest of the system
- Automatically disable certificate pinning along the way, capturing most of the hardest cases even normal ADB-powered setup can't intercept
This includes quite a few tricks to ensure that all traffic can be captured, and to disable various kinds of Frida & root/jailbreak detection as well. All the scripts are open source, so if you want to use & remix them yourself with Frida manually, it's easy to do: https://github.com/httptoolkit/frida-interception-and-unpinning/
Want to see what it can do? Try installing & intercepting the Android SSL Pinning Demo App to see how traffic using all modern pinning libraries is successfully captured.
Keylog Support
Pro users can now configure a keylog file in the HTTP Toolkit settings, which records the encryption keys for all incoming & outgoing connections.
Using this, you can use HTTP Toolkit together with tools like Wireshark, allowing you to easily intercept, inspect & modify traffic at the application level with HTTP Toolkit and inspect the raw byte-by-byte contents of every connection, including TLS fingerprint details, HTTP/2 framing, and any other low-level details that you might be interested in.
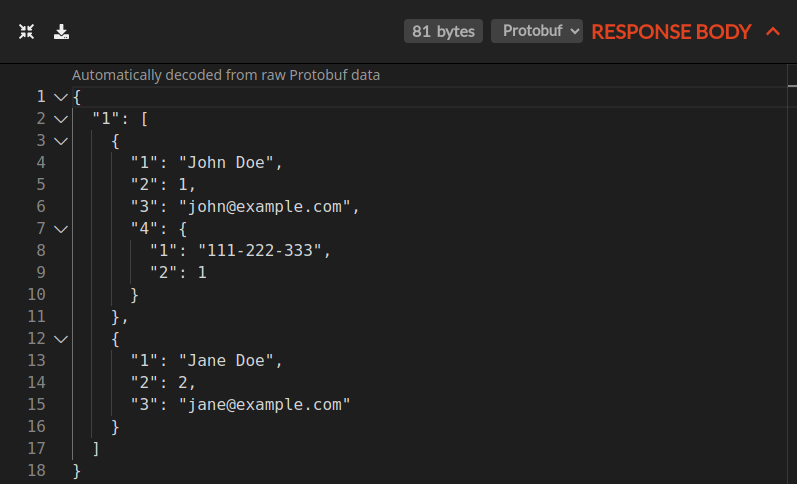
Protobuf & gRPC Inspection
HTTP Toolkit can now detect protobuf messages (with or without gRPC) and automatically decode them into raw data, with zero configuration or schemas required. This immediately turns a big blob of binary data into a readable structure that you can explore at your leisure.
Of course, this includes support for all your favourite edge cases too: compressed messages, multiple messages in a single body, gRPC over websockets, gRPC-JSON, you name it.
In future, this could also support custom schema for known APIs too - jump down to the end to vote for this if that sounds useful to you.
Traffic Perspectives
When proxying traffic through HTTP Toolkit, if you transform it en route, there's effectively multiple versions of the same request or response. There's the original request you received from the client, the transformed request that was forwarded to the server, and the equivalent server & maybe-modified client response on the way back (and that's before we even start talking about websockets and everything else).
Previously HTTP Toolkit always showed the client perspective (initial request, final response) but now whenever there's been a modification, you'll see a toggle on the request to switch between each interesting combination of perspectives: what the client saw, what the server saw, the original traffic in both directions or the modified traffic in both directions.
As part of this, all rows are also automatically marked with a little red pencil icon if any transformation has happened, along with a link taking you to the specific rule that was applied that's shown at the top when the row is selected.
Moving into a multi-perspective world like this has been a very complex change internally, but as a user this gives you a huge amount more visibility into exactly what's being proxied, so you can see how & where your rules are being applied and exactly what the before & after looks like.
Advanced Modify Rules
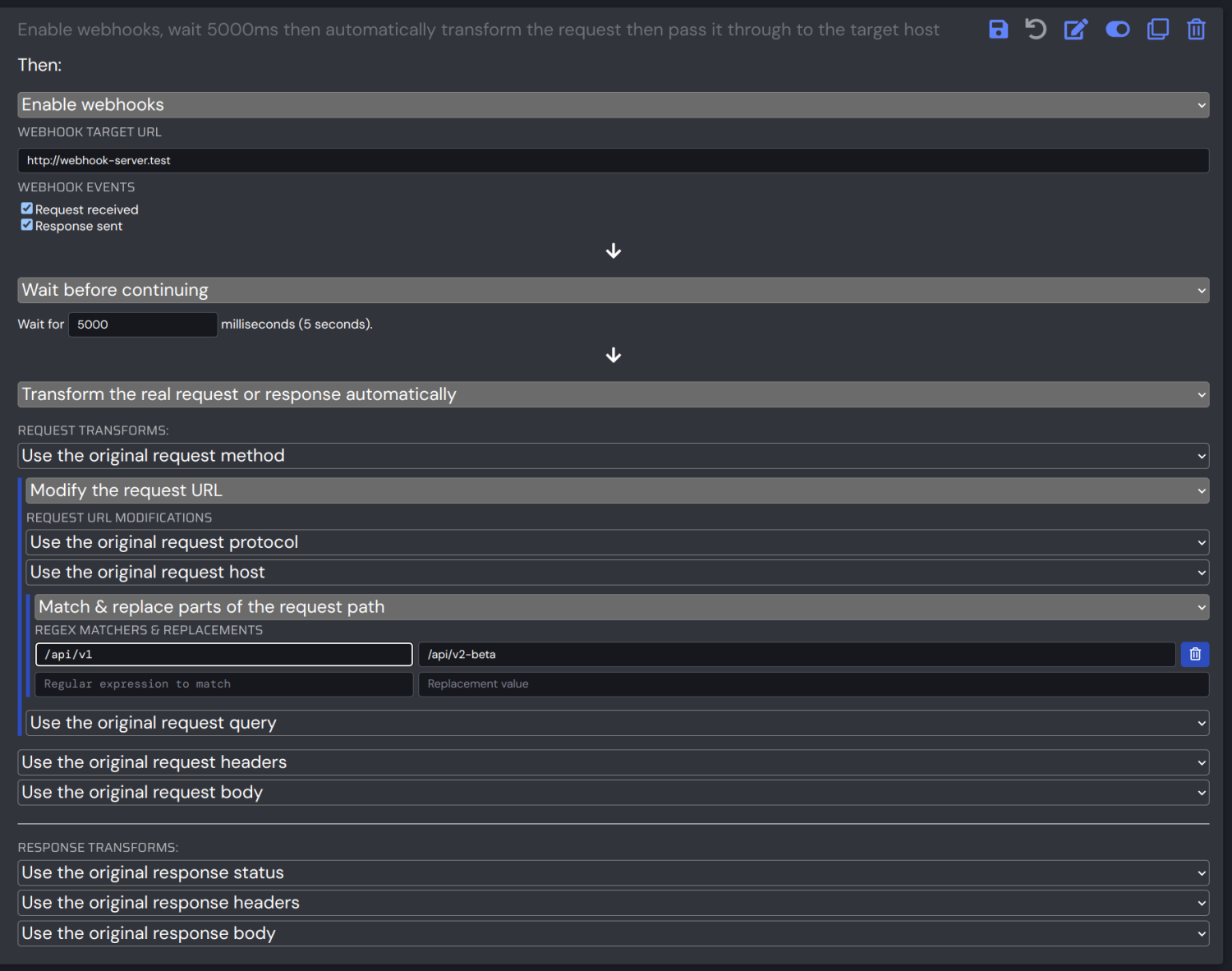
Speaking of rules & complex internal changes, HTTP Toolkit now supports:
- Multi-step rules (do X, then Y).
- Delay rules, allowing you to simulate latency, combinable with any other rule steps.
- Webhook rules, allowing you to log requests and/or responses from HTTP Toolkit into another API elsewhere, also combinable with any other rule steps.
- URL transformation rules, that let you define precise match-replace transformations on the host, path & query, replace them entirely, and override the protocol, so you can build complex traffic forwarding rules.
- Regex match-replace & JSON-patch body update rules, so you can precisely modify any part of any HTTP message body you're interested in.
There's a lot of new firepower here! With this, it's possible to define rules to do basically any transformation on any part of any request or response you might be interested in (want more similar powers over websocket traffic too? Jump to the end of the email and vote for it!)
Mockttp v4
Powering all of the low-level network interception within HTTP Toolkit is Mockttp. Mockttp offers all the interception power of HTTP Toolkit, as a headless open-source library, so you can build your own custom intercepting proxies or network automation.
Mockttp v4 was recently published, which includes the core of many of the features powering the rest of this email (all the rules changes described above, keylogging, multiple traffic events to capture perspectives, ...) and also some breaking changes along the way to tighten up behaviour and better support edge cases, particularly around traffic routing for tunneling cases like SOCKS. There's a detailed explanation of all the breaking changes here.
And more...
-
Huge performance & memory usage improvements - in intense processing scenarios where you're handling tens of thousands of requests a second (or importing an enormous HAR file) this can speed up traffic processing by up to 50x, and drop memory usage for the loaded data up to 40%.
- A complete website & product theme redesign, with a new logo, new colours, and dark mode everywhere (and custom theme support for Pro users too).
- Support for incoming SOCKS proxying, in addition to the existing normal HTTP proxying.
-
Pasted curl command support on the Send page - just paste a curl command into the URL bar and it'll autofill every field for you.
-
Stricter certificate generation, fully rewritten to closely follow the rules for real-world CAs to maximize support & trust with all clients.
- Automatic interception for Android TVs, the JVM up to Java 26 (before it's even released!), and more browsers including Firefox dev/nightly builds & Global Chromium.
-
Code snippet support for more languages, including Faraday in Ruby, Reqwest in Rust, Crystal, and Spring RestClient on the JVM.
-
Official ARM64 builds for both Mac (Apple Silicon) and Linux (want Windows ARM64 too? Vote here)
-
Context menus & new keyboard shortcuts throughout the UI for quicker access to more functionality.
- HTTP Toolkit is a founding member of the Open Source Pledge, committing to funding maintainers HTTP Toolkit depends on, and appearing in Times Square along the way.
- Last but not least, HTTP Toolkit recently hit 1 million downloads!
What's Next? Vote for Features!
Good question. There's a few big things in the works, and some other routes available - it's up to you!
Click any of the links to view the issue on GitHub, and add a thumbs-up there to vote for it. Feel free to vote for as many as you like, and you can also comment too to share any suggestions or feedback before design & development fully kicks off.
-
Automatic iOS interception. This has been on the list for quite a while, and I think it's definitely time. With this, the iOS experience will move from the current manual setup to a largely automated flow with its own app, just like Android.
-
Non-HTTP interception. By using SOCKS for interception (recently added) we can now carry extra connection metadata, meaning we can detect & successfully proxy most non-HTTP connections as well (including decrypting any TLS, as with HTTPS). This would let you see the raw bytes being transferred by these other protocols alongside your HTTP traffic, and reduce issues caused by interference with non-HTTP traffic especially on mobile devices.
-
Streaming support. Currently in most cases only completed messages are visible. If you want to debug server-side events, this can be problematic, since you can't see the data until the response finishes. Internally there is now the structure to dynamically stream data into the UI live - there's just a major UI refactoring required to use that and make it visible.
-
Public URL support. With a public URL (similar to ngrok/localtunnel/Cloudflare tunnels/etc) for your HTTP Toolkit instance, you could test webhooks, test OAuth flows and safely expose local servers remotely, with all the existing power of HTTP Toolkit on top to debug & modify traffic as it happens.
- View page improvements in the UI, allowing configurable columns & multiple row selections & actions.
-
Support for custom gRPC & protobuf schemas, to turn raw data into a fully parsed & structured format for known APIs.
-
System-wide interception. This would allow you to see everything sent from your Windows, Linux or Mac machine. Noisier than targeted interception but powerful for broad collection or awkward desktop apps.
-
WebSocket transform rules. Extending the existing WebSocket rules to support more transformations and automatic behaviours, similar to the many recent additions for plain HTTP.
-
Scripting support so you can write your own custom scripts within HTTP Toolkit to handle traffic dynamically in any way you like.
Please vote for whichever of these would be valuable to you! You can also explore the full list of issues, and submit your own ideas as well (but please check they haven't been submitted already first).
Oh, and don't forget - the BLACKFRIDAY25 deal on annual Pro accounts is only live until Tuesday! Support the project by signing up for HTTP Toolkit Pro now.
Have any other feedback or questions? Reply to this email and let me know.
|